November 2008

Install and Configure Cacti Monitoring tool in Ubuntu 8.10 (Intrepid Ibex) Server -- Ubuntu Geek
(via)
Developer's Guide - AJAX Libraries API - Google Code
October 2008

Midnight Research Labs - Depant your network

Box Backup - Trac

Xen Networking - Wiki

Funky Routing - OptionC
September 2008

Nimbus
Free File Hosting & Video Downloads, Free File Sharing, Online Friends Network - Ziddu
by 1 other (via)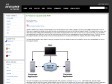
A Primer for OpenID with PHP | dev.aol.com | The AOL Developer Network
by 2 others
Mail Avenger
WiFiDog - Trac
by 2 othersAugust 2008

About Opsview | opsview.org
by 1 otherApril 2008
Logmonster FAQ - The Network People, Inc.

Openfiler — Openfiler Community
March 2008

Des cartes réseaux comme chez Free

Set Up Gateway Level Virus Security With ClamAV And SafeSquid Proxy | HowtoForge - Linux Howtos and Tutorials
February 2008

Greylisting: The Next Step in the Spam Control War
by 1 otherGlobule: the Open-Source Content Distribution Network
by 1 otherJanuary 2008
Welcome to the RESTORE Website

ClusterMonkey - Building A Virtual Cluster with Xen (Part One)

Using multiple network cards in XEN 3.0

IPerf: des exemples…
by 1 otherNovember 2007

CentOS / Red Hat Linux: Install and manage iSCSI Volume